How Safe Are Your Chrome Extensions, Really?
Navigating the balance between data privacy and technology use can be challenging, especially with Chrome extensions. In this post, we analyze the permissions and network traffic of extensions like QuillBot, revealing potential data risks even when idle. Learn how tools like Proxyman can help you...

If you are like me—someone who cares about data privacy but also relies heavily on useful tools and technologies—you might find yourself in a dilemma. The more we engage with various technologies and use different tools, the more data we have to share, or at least risk sharing unintentionally. In my humble opinion, one of the most sensitive areas is your browser.
Why?
You likely spend the whole day surfing the web, logging into your email, chatting on Facebook, making bank transfers, and much more. This makes your browser incredibly important but also vulnerable. I use Chrome and its extensions for my everyday personal and work-related tasks. Fortunately, the Chrome Web Store has robust app validation restrictions, preventing many threats to your security. However, any app developer must provide a list of permissions their application uses and explain why it needs those permissions when submitting to the store.
In this blog post, we will explore the safety of Chrome extensions by examining the permissions they request and analyzing their network traffic. We'll walk through how to use Proxyman to monitor an extension's behavior, using QuillBot as a real-world example.
Before we dive into this experiment, let's briefly discuss why the promised strong protection of the Chrome Store is not sufficient.
The Problem with Chrome Extensions
Chrome extensions can request permissions to read your browsing history, access URLs from other tabs, and much more. While these permissions are granted with the user's consent, there are two main issues:
- There are no technical restrictions ensuring that permission requests are used solely for the purposes stated by the developer. It's purely based on text-based approval.
- Users often don't pay close attention because they either value the added functionality the extension provides or they trust that the extension won't abuse their data.
Given these concerns, it's essential to be cautious about which Chrome extensions you install.
But what if an extension seems beneficial and necessary for your tasks? If you're unsure about an extension's trustworthiness and don't want to rely solely on user reviews, investing just 20 minutes of your time can provide valuable insights. You can examine the extension's code or analyze its network traffic to understand what data it handles and how it uses the permissions it requests.
In this post, we'll focus on analyzing network traffic using Proxyman. You can also use other tools like Wireshark to monitor what an extension does while you're using it and even when you're not.
For installation and usage instructions, please refer to the Proxyman documentation.
Real-World Scenario: Analyzing QuillBot Extension Traffic
I installed the QuillBot extension:
Next, I installed the necessary certificate:
In Proxyman, I activated a filter for the QuillBot extension and optionally enabled the interception of HTTPS responses, as shown below:
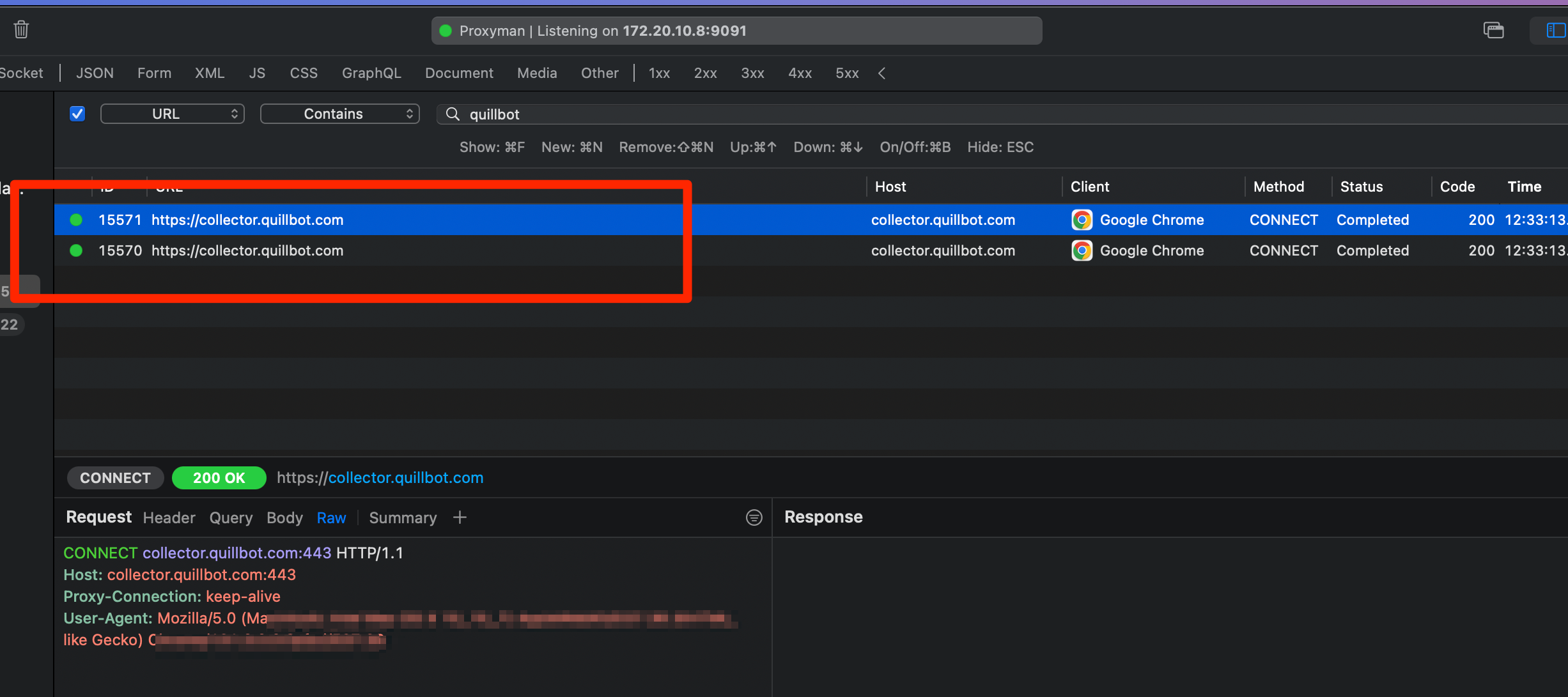
The Result:
While using QuillBot, I opened the extension as shown below:
Observing the traffic, there was some communication with the server—interesting but nothing particularly concerning.
However, the more revealing observation was what happened when I was notusing the extension:
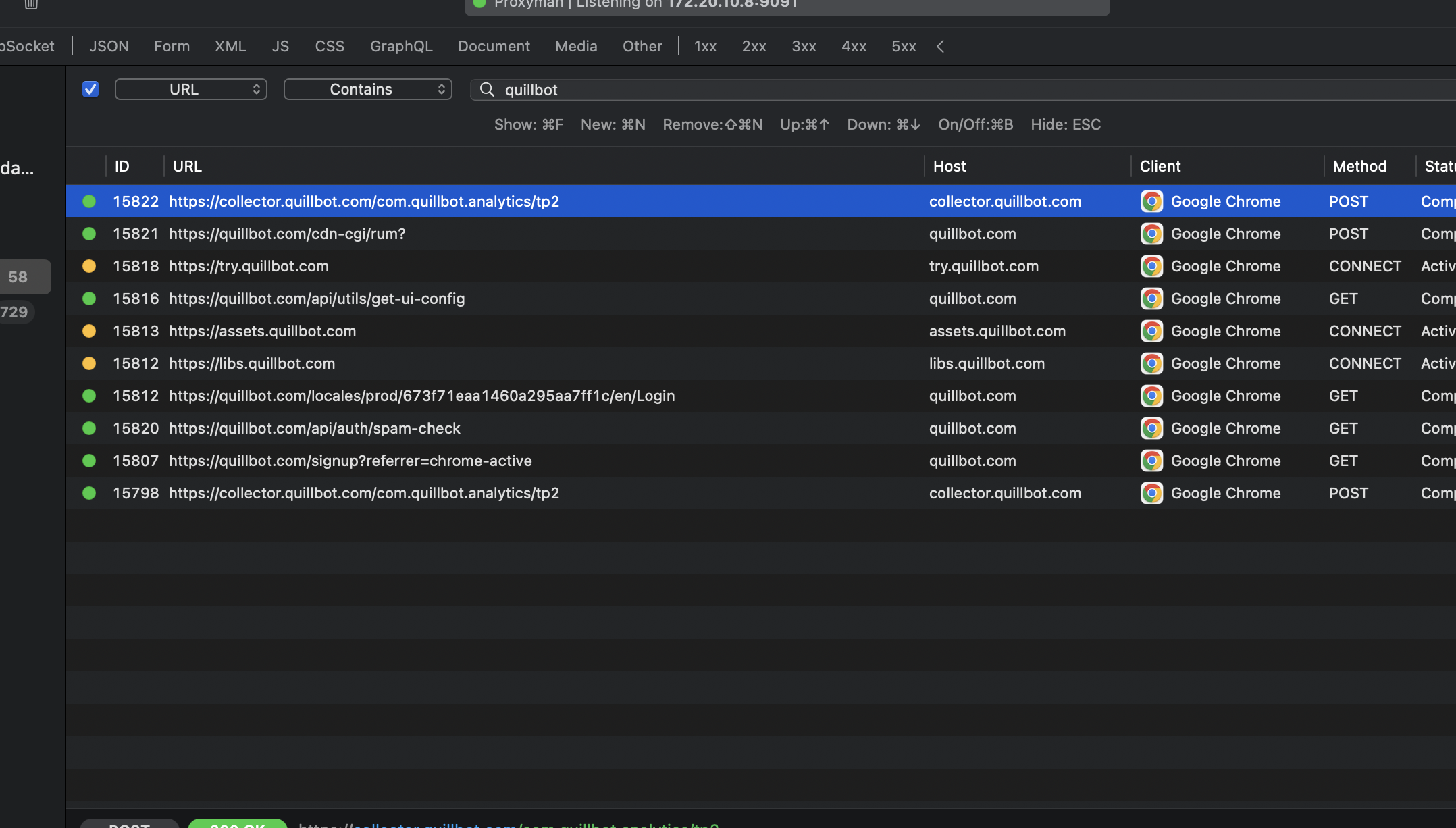
I first tested in standby mode, where I did not actively use the extension and expected it to remain silent:
But obviously, it was not. There was a considerable amount of traffic being transmitted back and forth:
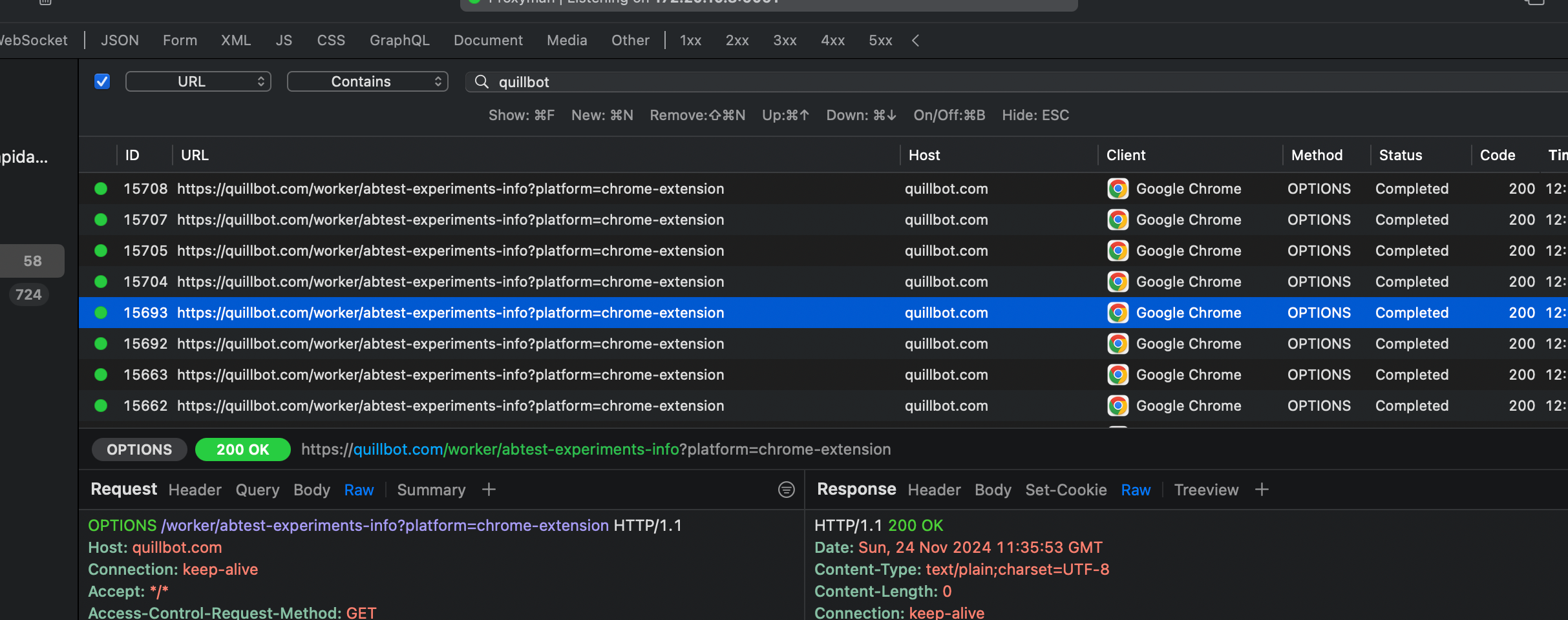
A quick look at the traffic revealed that the extension was transmitting my browser data every few seconds for some A/B testing purposes. While this is unusual, at least nothing more concerning was detected.
I felt a bit relieved, but since this is not the only extension I use, I strive to be very minimalistic with my extensions in general. Whenever I decide to use one, I either choose an extension that operates completely offline and/or is open-source. Additionally, I monitor the app's behavior and how it utilizes the permissions it claims to need for legitimate reasons.
Conclusion
In this exploration, we've taken a closer look at the safety of Chrome extensions by analyzing their permissions and network traffic. By using tools like Proxyman, we can gain insights into how extensions handle our data, both when actively in use and when idle.
While the Chrome Web Store does enforce certain security measures, it's ultimately up to users to remain vigilant about the extensions they install. By adopting a minimalistic approach and prioritizing extensions that are open-source or operate offline, we can better protect our data privacy without sacrificing the utility that these tools provide.




