Connect Claude to Gmail, Youtube, Notion and 100+ Data Sources with Zero Code
Explore the potential of the Model Context Protocol (MCP) in the AI ecosystem. MCP connects AI systems to essential data sources, enhancing performance while addressing security concerns like authentication. Tools such as Composio streamline secure connections through MCP, simplifying access to v...

If you follow my blog, you may have noticed my fascination with the Model Context Protocol (MCP) and its incredible power within AI ecosystems. It's a new standard designed to help AI assistants access the data they need to provide better answers. And I’m not alone. Since the standard was released, the MCP ecosystem has grown exponentially, with thousands of MCP servers now running around the world.
https://airabbit.blog/claude-integration-and-mcp-are-eating-the-world/
I’ve also talked about some of the challenges we face with this new technology. You can check my previous blog post to learn more about that.
https://airabbit.blog/five-mcp-risks-you-dont-want-in-production/
But one significant challenge is certainly security and authentication.
In this blog post, we will take a closer look at how authentication works when connecting AI systems based on MCP principles, and how different solutions and tools can improve security and speed up the connection process.
One such tool is Composio, which simplifies the process of creating connections and offering them via an MCP interface, following a similar approach to workflow tools like Zapier but with some differences we will also discuss.
https://airabbit.blog/connect-claude-desktop-to-7000-apis-with-5-lines-of-code/
If you just want to learn how to use Composio to create MCP servers for services, you can skip the intro. However, I would recommend taking a few minutes to read to get a deeper understanding of the possibilities and trade-offs when it comes to getting services connected for use with AI via MCP.
Let’s dive in.
Understanding How MCP Connections and Authentication Work
The Model Context Protocol (MCP), open-sourced by Anthropic, is a universal, open standard that connects AI assistants, such as Claude, to data-containing systems. The protocol's primary objective is to enable AI to access data sources directly or via dedicated MCP servers, thereby providing the necessary context for enhanced performance.
When connecting AI to various services or data sources, authentication is usually required. Many systems require a method of verifying the identity of users attempting to access them.
For example, a file system connection for AI might not need any authentication if it's local. But many connections are to online services that definitely require some kind of login or access method. For example, a web search using services like DuckDuckGo or Tavily would require an API key.
Authentication is required to connect to your email account, often through a process like OAuth. The same applies to Dropbox, Notion and all other services.
Some services provide an API key, while others use methods like OAuth.
Method 1: Using API Keys Directly
Let's say you want to connect a search engine like Tavily to Claude. You might add something like this to your Claude configuration, putting the API key right there in the file:
"tavily-mcp": {
"command": "npx",
"args": [
"-y",
"tavily-mcp@0.1.4"
],
"env": {
"TAVILY_API_KEY": "<< YOUR SUPER SECRET KEY GOES HERE >>"
},
"metadata": {
"quickAddTemplate": "tavily-mcp",
"templateName": "Tavily Search"
}
},
From a security standpoint, this isn't ideal. Storing all your sensitive API keys in a single configuration file means that if that file is compromised, an attacker could potentially gain access to all your important connected services.
Can we make it safer?
One way to make credentials more secure is to avoid entering them directly into client configurations. Instead, an external service or dedicated server component can establish the connection to the data source and securely store the keys.
Clients would then connect to this secure component, which would provide the data or functionality via a defined interface, such as MCP.
Claude > Secure Service/MCP Server (manages keys) > the target service (e.g., Google Mail)
Please note that this solution is not bulletproof either, because the connection information (basically a URL) to the remote MCP server has to be stored in plain text in your MCP client configuration.
Or, in the case of OAuth:
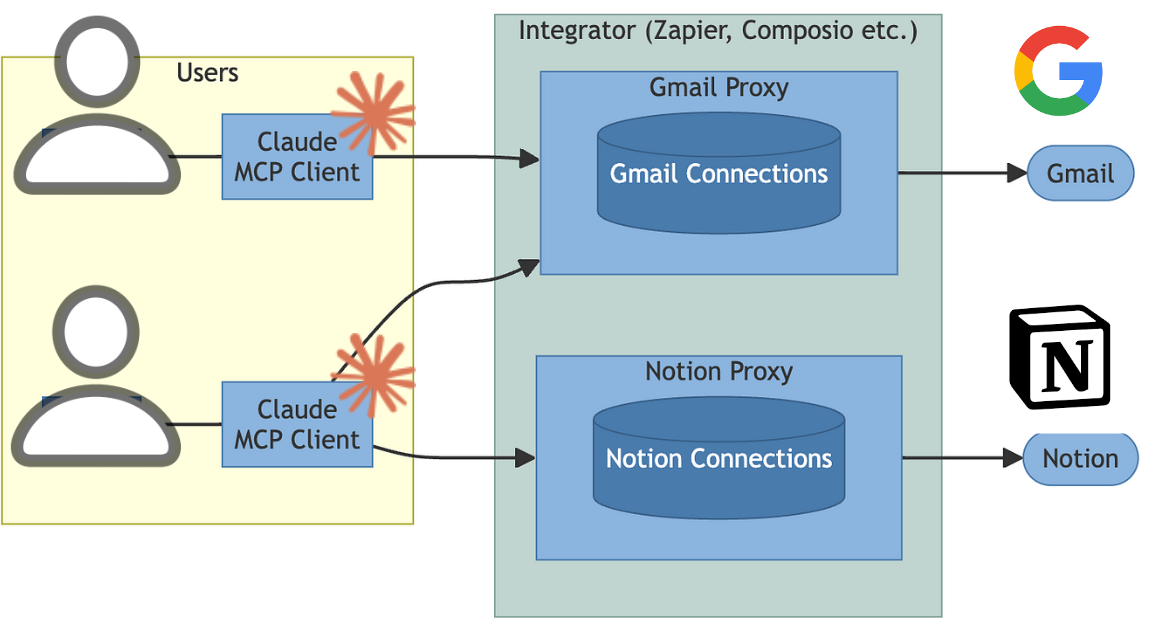
Claude > Secure Service/MCP Server (manages OAuth token after initiated) > the target service (e.g., Google Mail)
Using a local or cloud-based service to manage these connections and credentials can reduce the risk. If the service runs in the cloud, you don't need to install software packages (which could have security issues) on your machine, as these are usually managed by the service provider (e.g. Zapier, Compsio etc.)
